 WeTheNorth
WeTheNorth
 WeTheNorth
WeTheNorth
Complete WeTheNorth resources for anonymous marketplace access, Tor security, and cryptocurrency privacy in Canada

In 2025, digital privacy has become a fundamental right that Canadians must actively protect. As surveillance technologies advance and data collection becomes ubiquitous, understanding the tools and techniques for maintaining anonymity online is more critical than ever. This WeTheNorth guide provides Canadian users with essential security knowledge for navigating WeTheNorth marketplace and maintaining operational security.
The Canadian digital landscape presents unique challenges and opportunities for WeTheNorth users. With domestic-only transactions eliminating international customs risks and strong encryption standards, WeTheNorth members have access to strong privacy tools. However, law enforcement capabilities continue to evolve, making education about proper security practices essential for anyone seeking to maintain anonymity on WeTheNorth.
This WeTheNorth educational resource covers fundamental security concepts including Tor network architecture, PGP encryption implementation, cryptocurrency privacy best practices, and operational security principles. Whether you're new to WeTheNorth or seeking to enhance your existing knowledge, this guide provides practical, actionable information grounded in 2025's current security landscape.
Organizations like the Electronic Frontier Foundation (EFF) and the Tor Project continue to lead the fight for digital privacy rights. By understanding and implementing the security practices outlined in this WeTheNorth guide, Canadian users can protect their fundamental right to privacy while navigating WeTheNorth safely and responsibly.
Understanding three-node routing, exit node risks, and proper Tor Browser configuration for WeTheNorth users.
Learn More →Master key generation, message encryption, signature verification, and secure key management practices.
Learn More →Privacy comparison between Bitcoin and Monero for WeTheNorth, wallet security, and transaction anonymization techniques.
Learn More →Operational security fundamentals including compartmentalization, need-to-know basis, and threat modeling.
Learn More →Recognizing phishing attempts, verifying PGP signatures, and authenticating legitimate WeTheNorth mirrors.
Learn More →Curated collection of trusted privacy tools, organizations, and educational materials for Canadians.
Explore Resources →Real-time cryptocurrency market data relevant for anonymous transactions. Prices updated every 60 seconds from CoinGecko API.
Data Source: Real-time prices from CoinGecko. Market prices may vary across exchanges. Always verify current rates before executing transactions.

The Tor network provides anonymity through a sophisticated three-node routing architecture developed by the Tor Project. When you access a website through Tor, your connection passes through three randomly selected relays: an entry guard, a middle relay, and an exit node. Each node only knows the IP address of the previous and next node in the chain, making it virtually impossible to trace the original source of traffic.
For WeTheNorth users accessing the marketplace, this architecture provides critical privacy protection. Your Internet Service Provider (ISP) can see that you're connecting to the Tor network but cannot determine which websites you're visiting. The WeTheNorth server sees a connection from a Tor exit node, not your real IP address. This separation is essential for maintaining anonymity in 2025's surveillance environment.
However, Tor is not foolproof. Exit nodes can monitor unencrypted traffic, which is why accessing WeTheNorth .onion hidden services (which never leave the Tor network) is significantly safer than accessing regular websites through Tor. WeTheNorth users should exclusively use .onion addresses and verify they're connecting to authenticated WeTheNorth mirrors to ensure end-to-end encryption within the Tor network.
Advanced threats include traffic correlation attacks, where adversaries controlling both entry and exit nodes can potentially correlate traffic patterns. While sophisticated, these attacks require significant resources and are primarily a concern for high-value targets. For most WeTheNorth users, properly configured Tor Browser provides solid anonymity against common surveillance techniques.
Proper Tor Browser configuration is critical for maintaining anonymity. Always download Tor Browser exclusively from the official Tor Project website to avoid compromised versions. For WeTheNorth users, downloading directly from the official source ensures you receive the authentic, unmodified browser with all security features intact.
Set your Tor Browser security level to "Safest" immediately after installation. This disables JavaScript by default, which eliminates many attack vectors used to de-anonymize users. While this breaks some website functionality, anonymous marketplaces are designed to work without JavaScript. The security trade-off is absolutely worth the minor inconvenience for WeTheNorth users prioritizing anonymity.
Never maximize your Tor Browser window. Browser fingerprinting techniques can identify users based on screen resolution and window size. Tor Browser's default window size is shared by millions of users, making you indistinguishable from the crowd. Maximizing the window reveals your unique screen resolution, potentially compromising anonymity. This simple practice significantly enhances privacy protection.
Consider using Tails OS or Whonix for enhanced security. Tails is a live operating system that routes all traffic through Tor and leaves no trace on your computer. Whonix uses virtualization to isolate Tor traffic from potential system-level compromises. For WeTheNorth users conducting sensitive marketplace transactions, these operating systems provide additional security layers beyond standard Tor Browser usage.
Pretty Good Privacy (PGP) encryption is essential for secure communication on WeTheNorth marketplace. PGP uses asymmetric cryptography with a public key (shared openly) and a private key (kept secret). WeTheNorth users must generate strong PGP keys using tools like GnuPG (GPG), which implements the OpenPGP standard.
Generate a 4096-bit RSA key pair as the minimum standard in 2025. Smaller key sizes (2048-bit) are still technically secure but 4096-bit provides future-proofing against advancing computational power. When creating your key, use a strong passphrase that you'll remember but others cannot guess. This passphrase protects your private key if your device is compromised—without it, the private key is useless to attackers.
Your public key should be uploaded to your WeTheNorth profile, allowing vendors and administrators to send you encrypted messages that only you can decrypt. Never share your private key with anyone—it's the cryptographic equivalent of a house key. Store your private key securely, preferably on an encrypted USB drive stored separately from your computer. Consider creating a revocation certificate immediately after key generation in case you need to invalidate the key due to compromise.
Key management extends beyond creation. Regularly back up your private key to multiple secure locations. If you lose your private key, you permanently lose access to all messages encrypted with your public key. For WeTheNorth users, this means losing access to important shipping information, dispute communications, and transaction records. Proper key management is non-negotiable for WeTheNorth operational security.
Encrypting messages with PGP ensures that only the intended recipient can read your communications. On WeTheNorth, encrypt all sensitive information including shipping addresses, phone numbers, and transaction details. To encrypt a message, you need the recipient's public key. Import their public key into your keyring, compose your message, and encrypt it using their public key. The resulting ciphertext appears as random characters that only the recipient's private key can decrypt.
Digital signatures authenticate message senders and verify message integrity. When a vendor signs a message with their private key, you can verify the signature using their public key. This proves two critical facts: the message genuinely came from the vendor (authentication) and the message wasn't modified in transit (integrity). WeTheNorth users should verify PGP signatures on all marketplace communications, especially mirror lists and administrative announcements.
Phishing attacks on anonymous marketplaces are common. Attackers create fake mirrors or impersonate vendors to steal credentials and funds. PGP signature verification is your primary defense. Before trusting any mirror link or vendor communication, verify the PGP signature against the known public key. If the signature verification fails or the public key fingerprint doesn't match, you're likely dealing with a phishing attempt. Never proceed without verified signatures.
Practice PGP encryption and decryption before conducting real WeTheNorth transactions. Generate test messages, encrypt them with your own public key, and decrypt them with your private key. This familiarization process ensures you understand the workflow when real stakes are involved. Many WeTheNorth users have lost funds due to incorrect address encryption or failed message decryption. Competence with PGP is not optional—it's a fundamental WeTheNorth security requirement.
Bitcoin, while revolutionary, offers limited privacy for WeTheNorth marketplace transactions. Every Bitcoin transaction is permanently recorded on a public blockchain visible to anyone. Blockchain analysis companies like Chainalysis work with law enforcement to trace Bitcoin flows, identifying users through exchange KYC records, IP address leaks, and transaction pattern analysis. For WeTheNorth users, Bitcoin transactions are traceable and can potentially be linked to real-world identities.
In 2025, Canadian cryptocurrency exchanges are required to collect Know Your Customer (KYC) information including government ID, proof of address, and banking details. When you purchase Bitcoin through a Canadian exchange like Coinsquare or NDAX, your identity is permanently linked to those coins. If you directly deposit these coins to WeTheNorth, law enforcement can trace the flow from exchange (known identity) to WeTheNorth deposit address. This creates a prosecutable evidence trail.
Bitcoin mixing services and CoinJoin transactions can improve privacy by obfuscating transaction trails, but they're not foolproof. Advanced blockchain analysis can sometimes de-anonymize mixed coins through heuristic analysis and pattern recognition. Additionally, many exchanges now flag coins from mixing services as high-risk, potentially freezing your account. For WeTheNorth users seeking genuine privacy, Bitcoin presents significant challenges despite mitigation techniques.
If using Bitcoin for WeTheNorth transactions, employ strict operational security: never reuse addresses, avoid direct exchange-to-WeTheNorth transfers (use intermediate wallets), consider CoinJoin transactions, and use a dedicated Bitcoin wallet separate from other financial activities. However, understand that Bitcoin provides pseudonymity (identity hidden behind addresses) rather than true anonymity. For maximum WeTheNorth privacy, cryptocurrency designed specifically for anonymity is superior. Learn more at Bitcoin.org.
Monero (XMR) is designed specifically for private transactions, making it the preferred cryptocurrency for WeTheNorth marketplace in 2025. Unlike Bitcoin's transparent blockchain, Monero transactions use ring signatures, stealth addresses, and RingCT to obscure sender, receiver, and transaction amounts. Every Monero transaction is private by default—there's no public record of who sent how much to whom. For WeTheNorth users prioritizing privacy, Monero is the superior choice.
Ring signatures mix your transaction with several other unrelated transactions, making it cryptographically impossible to determine which is the real sender. Stealth addresses generate unique one-time addresses for each transaction, preventing address reuse tracking. RingCT (Ring Confidential Transactions) hides transaction amounts using cryptographic commitments. These three technologies combine to provide complete transaction privacy that blockchain analysis cannot break.
Acquiring Monero while maintaining privacy requires careful approach. Canadian exchanges increasingly offer XMR, but purchasing creates the same KYC linkage as Bitcoin. Better strategies include: using decentralized exchanges (DEXs) that don't require KYC, buying Bitcoin peer-to-peer and exchanging to Monero, or using Bitcoin ATMs and converting to XMR. Each method has trade-offs between convenience, cost, and privacy. Research current options carefully before acquiring XMR.
Store Monero in the official Monero GUI or CLI wallet rather than exchange wallets. Full node wallets provide maximum privacy and security by not relying on third-party servers. While syncing the Monero blockchain takes time and storage space, the privacy and security benefits are worth the investment for serious Canadian marketplace users. Hardware wallet support for Monero (Ledger, Trezor) combines convenience with security for larger holdings.

Strong, unique passwords are fundamental to marketplace account security. In 2025, password best practices have evolved beyond simple complexity requirements. The most secure passwords are long passphrases: random combinations of multiple words that are easy to remember but difficult to crack. For example, "correct-horse-battery-staple" is far more secure than "P@ssw0rd123!" despite appearing simpler.
Never reuse passwords across different services. If one site suffers a data breach, credential stuffing attacks will attempt your leaked password on every major service. Canadian marketplace users must use completely unique passwords for each account: email, cryptocurrency exchanges, marketplace accounts, and PGP key passphrases should all be different. Password reuse is one of the most common security failures leading to account compromise.
Use a password manager like KeePassXC to generate and store complex passwords securely. KeePassXC is open-source, fully offline, and encrypts your password database with a master password. Store the encrypted database on a USB drive separate from your computer. This approach provides excellent security while maintaining usability—you only need to remember one strong master password to access all your other passwords.
Two-factor authentication (2FA) adds critical additional security. When available, enable 2FA on marketplace accounts and cryptocurrency exchanges. PGP-based 2FA is common on anonymous marketplaces, requiring you to sign a challenge with your PGP private key during login. This ensures that even if someone steals your password, they cannot access your account without your PGP private key. For Canadian users, 2FA is essential protection against account takeover attacks.
Phishing attacks targeting anonymous marketplace users are extremely common in 2025. Attackers create fake mirrors that look identical to legitimate marketplaces, stealing credentials and cryptocurrency from unsuspecting users. Canadian users must verify every mirror link before logging in. Never trust links from forums, random websites, or unverified sources. Always cross-reference mirror lists from multiple independent trusted sources.
V3 onion addresses are 56 characters long and end in .onion. Legitimate marketplaces use v3 addresses for enhanced security and cryptographic verification. If you encounter a shorter v2 address (16 characters), be extremely suspicious—v2 addresses are deprecated and likely phishing attempts. Always verify the complete onion address character-by-character before accessing. A single character difference represents a completely different site, likely malicious.
PGP signature verification is your primary defense against phishing. Official marketplace administrators sign their mirror lists with their PGP private key. Download the signed mirror list, verify the signature using the administrator's public key (obtained from multiple trusted sources), and only trust mirrors listed in verified signed messages. If you cannot verify a PGP signature, do not trust the mirror—the risk of compromise is too high.
Bookmark verified mirrors in Tor Browser immediately after verification. This reduces the risk of future phishing as you can access the marketplace directly from bookmarks rather than searching for links. However, periodically re-verify your bookmarks against newly signed mirror lists, as legitimate mirrors can go offline and new ones emerge. Operational security requires ongoing vigilance, not one-time verification. Stay informed about current verified mirrors and phishing threats.
Operational security (OPSEC) is the practice of protecting critical information from adversaries. For Canadian marketplace users, OPSEC means preventing law enforcement, hackers, and other threats from connecting your online activities to your real identity. Strong OPSEC requires consistent application of security principles across all aspects of your digital life. A single mistake can compromise months or years of careful operational security.
Compartmentalization is the foundation of effective OPSEC. Never mix your anonymous marketplace activities with your real identity. Use dedicated devices, operating systems, email addresses, cryptocurrency wallets, and personas exclusively for marketplace use. Your marketplace laptop should never access Facebook, Gmail, or any services linked to your real name. This separation ensures that if one compartment is compromised, others remain secure.
Need-to-know basis means sharing information only with those who absolutely require it. Never discuss marketplace activities with friends, family, or acquaintances. Every person you tell becomes a potential security vulnerability—they could be arrested and compelled to testify, their devices could be seized containing your conversations, or they could simply make mistakes and reveal information unintentionally. The fewer people who know about your activities, the smaller your attack surface.
Assume compromise means operating as if adversaries are actively monitoring you. Don't discuss future plans in unencrypted communications. Don't leave obvious evidence on devices that could be seized. Maintain deniability wherever possible. For Canadian users, this mindset prevents complacency and ensures consistent security practices. When in doubt about a security decision, choose the more cautious option. Paranoia is justified—numerous marketplace users have been prosecuted due to OPSEC failures.
Curated collection of trusted privacy tools, organizations, and educational materials for Canadian users seeking to enhance their digital security.
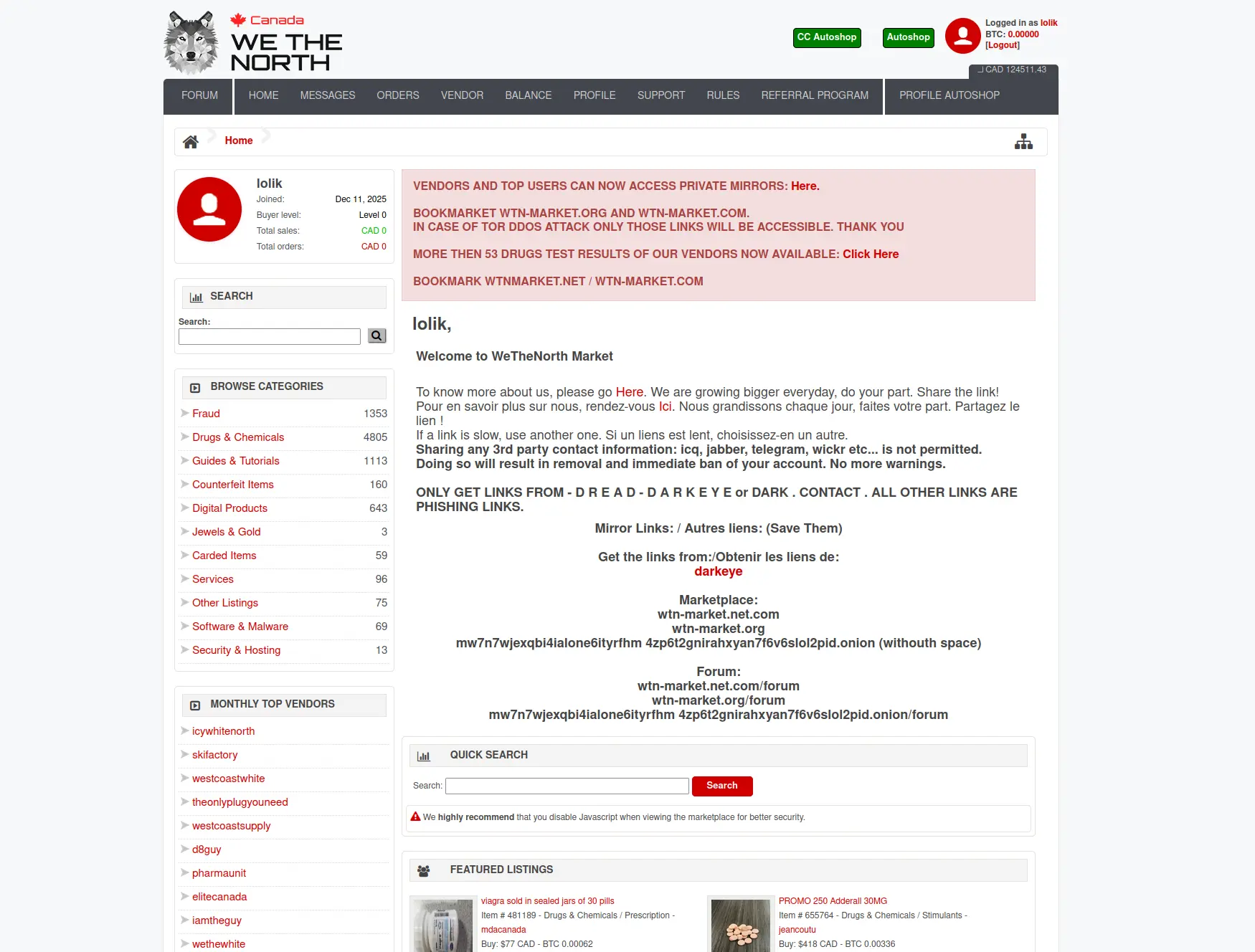
Visual overview of marketplace security features and user interface elements.
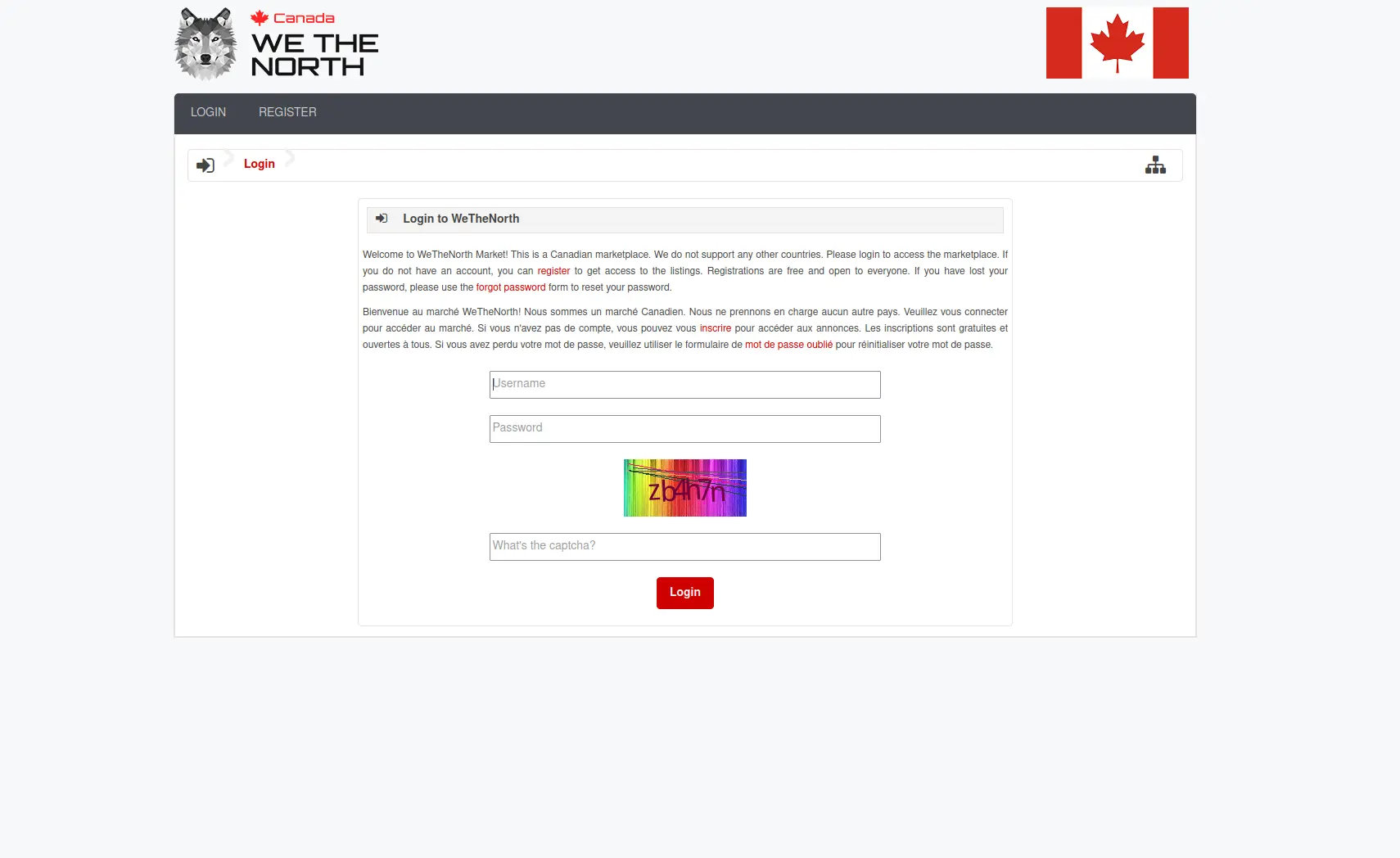
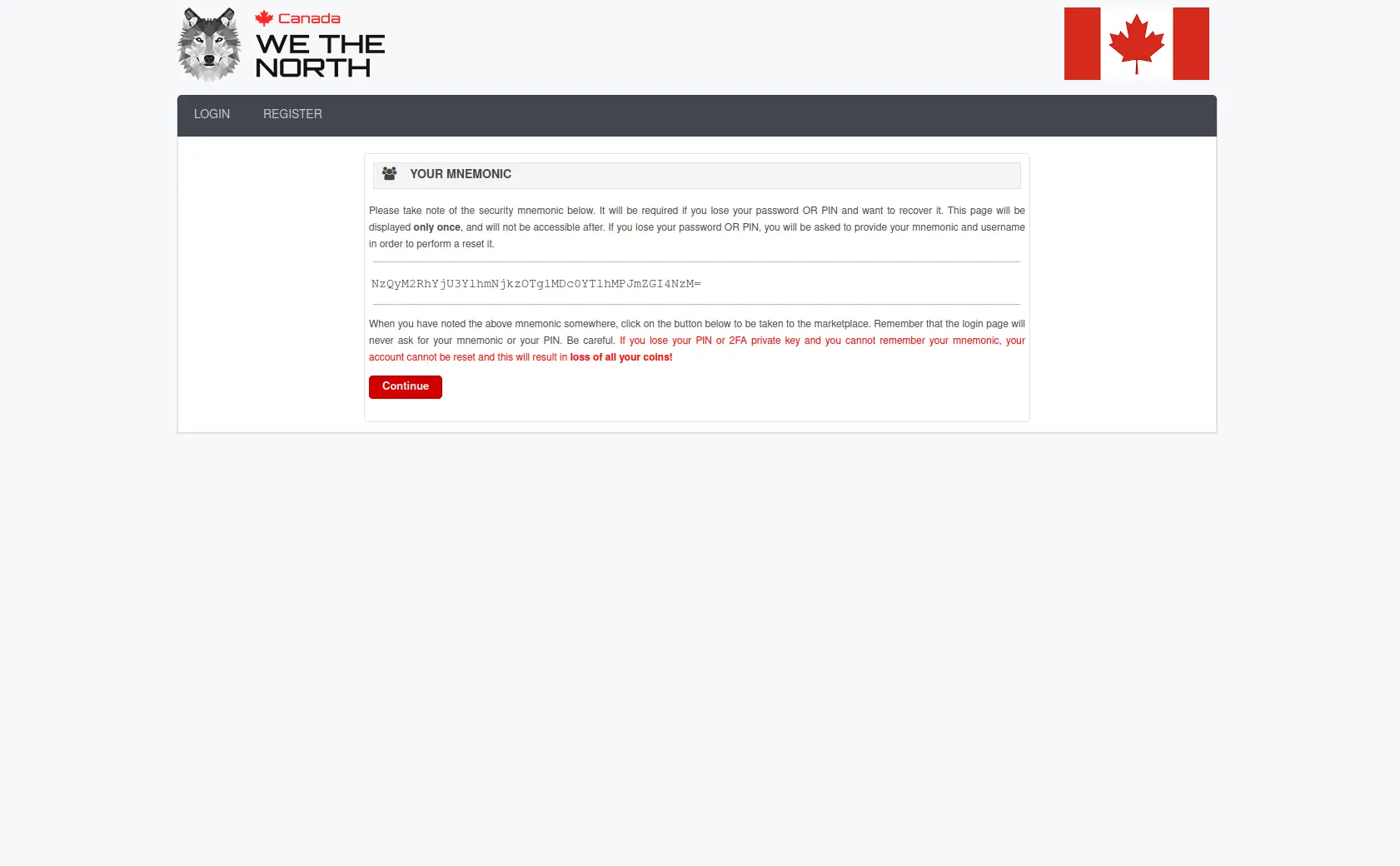
Secure Login Interface
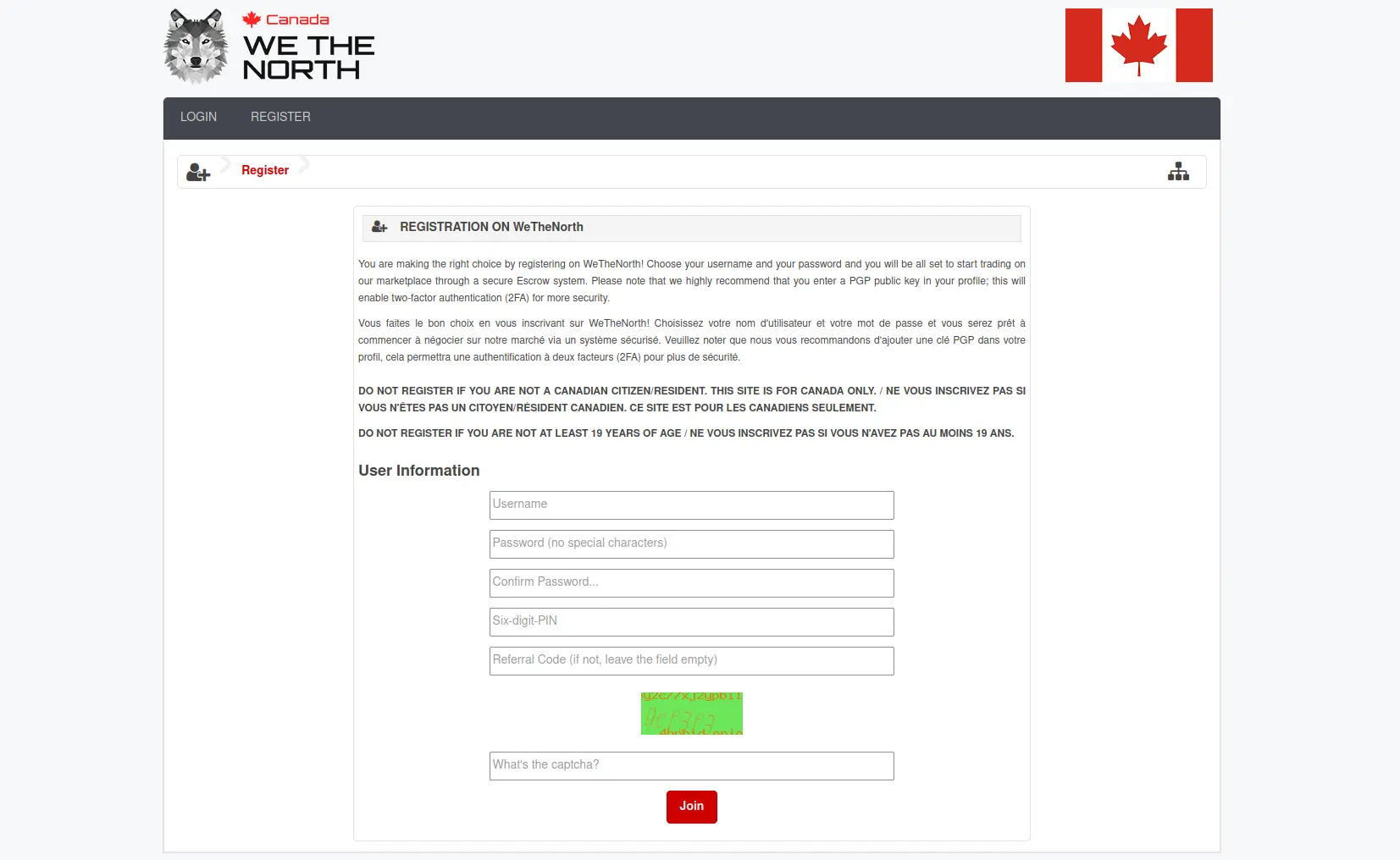
Registration Process

Security Verification

Wallet Recovery Backup

Encrypted Storage

Secure Connections
Learn about platform features, bilingual support, Canadian domestic shipping advantages, and security implementation since 2021.
Learn More →Full security documentation covering escrow systems, PGP 2FA authentication, and operational security best practices.
Read Security →View verified marketplace mirrors with real-time status monitoring, PGP signature verification, and connection instructions.
Access Now →Frequently asked questions about registration, deposits, escrow, bilingual support, and Canadian shipping policies.
View FAQ →🕒 Page last updated: